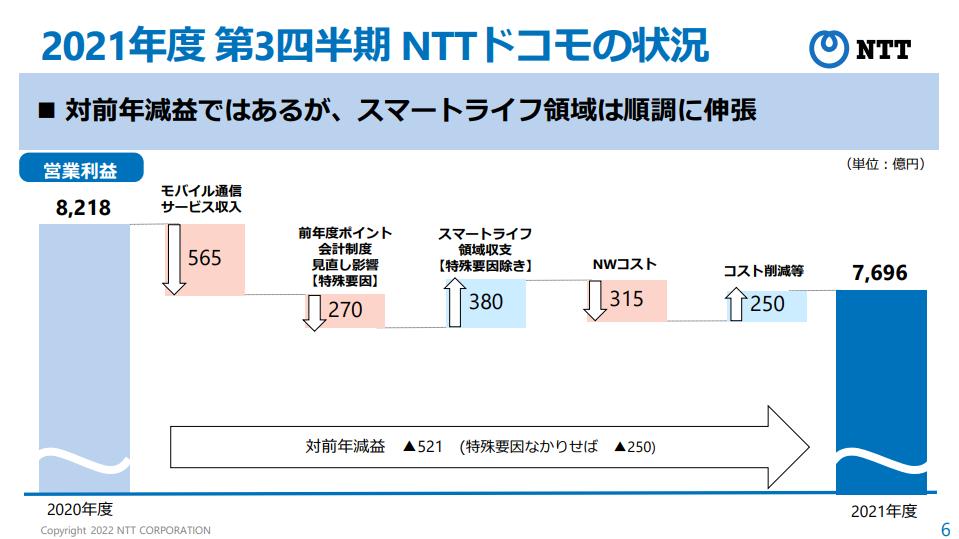
The garage de elements are also hacked
The idea of controlling the garage door remotely to confirm that your home is safe, or have the garage directly delivered your luggage is attractive to many people.Consumers stop thinking about potential security issues due to this convenience provided by many IoT devices.
McAfee ATR has recently investigated MYQ HUB of "Universal" garage door automatic opening and closing platform Chamberlain.CHAMBERLAIN has made this device universal by going through a hub that functions as a new garage door opening and closing device, like the switch in the car.In this way, MYQ HUB will be able to improve and link various garage doors.
Regarding the protection of this device, which is usually not common as an IoT device, it turns out that Chamberlain is doing a pretty good job.However, we found that MYQ HUB has a defect in how to communicate with a remote sensor via a radio frequency.
From an attack perspective, there are three attack routes we started investigating.Local network, remote access (API, or third -party integration), RF communication between sensors and hubs.The first thing I tried was to access the device via a local network.The quick port scan reveals that the device is liston on port 80.If you try to move to the device with port 80, Start.Redirected to HTML and a 404 error is returned.There is no other port open on the device.
Inside of Chamberlain Myq Hub
When the hub is disassembled, a secondary PIC microcontroller that controls both the RF side of both the small SOC (System on a chip) module that handles Wi-Fi and web communication, and the RF side of both the garage door and remote door sensor.The MyQ hub on the FCC website also included a Bluetooth module that we purchased.
The UART connection was cut or not enabled, but the JTAG connection was working to directly communicate with the main Wi-Fi module.With the JTAG connection, the entire flash chip content was dumped and the system could be debugged unlimitedly.The main Wi-Fi module was a marvel micro controller that runs RTOS (Real Time Operating System), which works greatly from the normal Linux system.We continue to perform pre -defined applications, but RTOS does not usually have a file system that the conventional system had.I was able to extract the entire content of MARVELL microcessesa to analyze assembly and the operation of the web server.
By checking the web server code, we identified how the device was set up via the local API, and found a good but interesting command.
Local API command
There were some URLs and additional API paths that were found to be accessible, but there was no noticeable place to start attacking.At this point, I decided to investigate other attack routes.
We didn't take much time to investigate the third -party attack path and remote API. In the survey, this is an ambiguous area. While testing with/sys/mode API calling, the device was set up in a software factory. You can now try adding a device to another account. When I captured SSL traffic in a mobile application, I realized that the serial number had failed because it was already registered in another account. Traffic from Android applications has been deciphered using the technology called SSL pin release. To explain this process in more detail, post a new blog. What we wanted to try was to change the Android app to send another serial number. You may have been able to open the device from a new account because the device is unlikely to erase the original garage door information. However, this is all guessed and has not been tested because it does not want to access the remote API.
The last surveyed route was RF.We have started analyzing the frequency modulation between the remote door sensor and the hub.Initially, I thought it was like FSK (Frequency Shift Keying), where the data is sent digital.If the signal is in one frequency, the corresponding bit is 0, and the signal is displayed at another frequency, the bit is 1.This idea was abandoned because the MyQ remote sensor used not only two but also three different frequencies.
Looking at the FCC filing of the door sensor, I noticed a particularly effective correction.
OOK stands for "on -off keying" and is another way to encode digital bit into RF.OOK is either sending a signal (1) or not sending a signal (0).This means that you need to synchronize both the transmitter and the receiver.
On -off keying graphical expression
This is a binary expression of the signal captured by the MyQ remote door sensor.This is a window where the entire signal is enlarged.
One complete message is captured and each color indicates a different frequency

You can observe the status of the transmission that is captured from all three frequencies and has been converted to hexadecimal numbers. As shown by color above, it is easy to identify the data pattern in the transmitted, but it is not possible to crack from our SDR (Software Defined Radio) to send the False status. was. It also shows that CHAMBERLAIN RF engineers not only separate signals into three different frequencies, but also implement security by implementing rolling codes. Rolling code technology may be familiar, depending on the standard garage door opener or car key fob. Rolling code devices prevent the attacker from capturing the signal directly and replaying. This is prevented by a signal including the unique identifier recorded by the recipient. If the recipient finds the signal with a unique ID again, ignore it.
The way the attacker overcomes a rolling code device is called "roll jam". The attacker interferes with the rolling code signal from the transmitter, blocks it so that it does not reach the receiver, and captures and preserves valid rolling codes. In this way, the attacker gets unused and effective rolling codes that the recipient has never seen before. It should be noted in this method that the victims usually have not unlocked the garage door or car. The more difficult way to notice a roll jam is to always capture the latest code and replay one of the latest signals. In this way, cars and doors will open, but the attacker still owns the latest code to use it yourself.
MyQ also had a rolling code that enables the development of variations of this technology.We have adopted the concept of sending a large amount of "noise" directly adjacent to the valid signal frequency to hinder the original code from the receiver.This causes the MYQ HUB receiver to overload and cannot hear valid signals.However, due to the accuracy of the SDR, the signal was saved, ignoring the noise we are sending.The fact that the three frequencies must be hindered at the same time and obstructing them, which has become more complicated.If you are interested in this FHSS (FREQUENCY HOPPING SPECTRUM) roll jam technology, please read our white paper
In a survey related to Chamberlain's garage door hub described in this blog, the only interference was for the unlicensed shortest radio frequency spectrum.On the other hand, the garage door hub transmitted a state signal, and there was no interference on the communication or permitted communication signal based on the Communications Law or FCC rules.
This technology has worked, but the reliability has been reduced because the remote sensor and the MYQ hub are always dominant under the RF situation.The aspect of the obstruction of the attack has worked well.However, we are outside the garage, both remote sensors and hubs are inside the same garage, and the garage door and walls function as barriers, so it is difficult to do herself and listen at the same time.By ignoring a high -output radio, frequency adjustment antenna, and the FCC method, the obstruction of the remote sensor can be much farther than the tests possible in our lab environment.
Remote sensor signal (red) and obstruction (black) waterfall view
In a situation where our obstruction is ensured, it is confirmed that the remote sensor is absolutely closed because the user is obstructing when the user closes the garage door via the MyQ application. Did. The app warns the user, "Something has occurred. Try it again." Then, if you can't see the garage door directly, you'll think that ordinary users have a garage door open, even though they are actually closed. If the user believes in the MyQ app, "retry" as the application shows. This is where the stateless state of the garage door works. The door opens when the MyQ hub sends the opening and closing signal to the garage door. Because the door is already closed, and the hub simply changes the state. This allows the attacker to enter the garage directly. And in many cases, it enters the house.
If the garage door actually opens, the attacker will probably not want to keep it as it is, as it will inform the victim that the problem has occurred again.The victim is relieved if the garage door is closed and the app can erase the error.This is a replay from a signal where the previously captured door is closed, or the simplest method is to remove the remote sensor from the garage door Velcro and install it vertically.Inform the hub that it has been closed properly.
Attack reproduction status flow chart
Also, in the real world scenario, I realized that the attacker could not sit out of the garage all day long, so I decided to automate the attack.We have implemented JIT (Just in Time) means using GNU Radio.There, the three individual frequencies of MyQ are liston while the SDR is pause.The moment you know that the remote door sensor has started sending, start after dynamically enabling signal obstruction.
GNU Radio JIT obstruction and three simultaneous frequencies capture
Therefore, if a small device to be installed in an invisible place near the garage door is created, the use case of this type of attack will increase.Our FHSS white paper describes this technology in more detail.The specification of the device position using the RF triangle surveying becomes very difficult due to JIT obstruction, and the battery operation can be more appropriate.
This may not be very common for individuals who use the MyQ hub, but remember what I mentioned earlier about the third -party partnership with MyQ for garage delivery. Another possible attack is when the delivery driver uses the application. The main reason for users to sign up to this service is that they can deliver their luggage to a safe place (garage) even when they are not at home. If the delivery driver uses the MyQ hub for in -garage delivery, the victim can open and close the garage door via the MyQ app on the Internet, even if it is not there. A solid hacker will do this attack, and the possibility that the victim will believe that the door is actually open is even higher. Survey results, including detailed reproduction procedures for obstruction attacks, were disclosed to Chamberlain on September 25, 2019. I told Chamberlain about this issue about the third party delivery driver and how it applies to this attack model. After a wide range of tests and verification of problems, the vendor is version 4.145.1.As of 36946, we released the MYQ app update.This update provides a valuable warning message that indicates that the state of the garage door may not be accurate, but does not exclude the remote control of the door itself by the user.
The advantage of the IoT device is to solve the problem that you need to deal with. If you experience the convenience and how these devices automate our lives, secure, or support them, you will no longer let go of them. This simplicity and automation often hide the approaching potential security threats. This effect also has a simple enhancement of manual products over time. For example, a garage door opener that is now in a car in a car. The threat has been converted from a physical space to a digital space by capturing and replaying basic signals. CHAMBERLAIN's MyQ hub ultimately creates a more secure garage than previous products, but consumers have any technical platforms, such as the use of WiFi, mobile apps, and FHSS RF transmission. It is important to note that there is a possibility of expanding the path of potential threats.
Finally, based on the complexity and installation area of the attack, I would like to conclude that the actual attack on this target is low.We verified the results of the survey and discussed this with Chamberlain, who has agreed to the evaluation.Chamberlain has clearly strived to build a secure product.And it seems to have excluded many of the easy achievements that are common to IoT devices.It's nice to be able to cooperate with this vendor.They clearly prioritize security as a prospect of product development.
注釈:In a survey related to Chamberlain's garage door hub described in this blog, the only interference was for the unlicensed shortest radio frequency spectrum.On the other hand, the garage door hub transmitted a state signal, and there was no interference on the communication or permitted communication signal based on the Communications Law or FCC rules.
* The content of this page is an abstract of the MCAFEE BLOG updated on January 6, 2020 (US time).Original text: WE BE JAMMIN ' - Bypassing Chamberlain MyQ Garage Doors Author: Sam Quinn, Steve Povolny and Kevin MCgrath
■ Related site